* web/flows: bottom-align about text on flows page Signed-off-by: Jens Langhammer <jens@goauthentik.io> * fix a bunch of typos Signed-off-by: Jens Langhammer <jens@goauthentik.io> --------- Signed-off-by: Jens Langhammer <jens@goauthentik.io>
2.8 KiB
| title |
|---|
| organizr |
Support level: Community
What is organizr
Organizr allows you to setup "Tabs" that will be loaded all in one webpage.
This integration leverages authentik's LDAP for the identity provider to achieve an SSO experience. See ldap provider generic setup for setting up the LDAP provider.
Preparation
The following placeholders will be used:
organizr.companyis the FQDN of the Service install.authentik.companyis the FQDN of the authentik install.
Create a new user account (or reuse an existing) for organizr to use for LDAP bind under Directory -> Users -> Create, in this example called ldapservice.
Note the DN of this user will be `cn=ldapservice,ou=users,dc=ldap,dc=goauthentik,dc=io`
:::tip
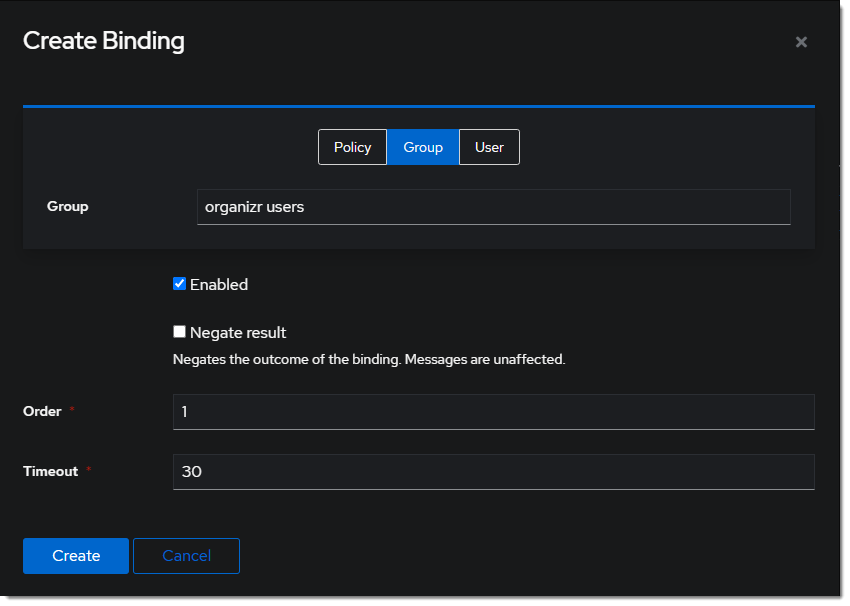
Optionally, create a new group like organizr users to scope access to the organizr application.
:::
authentik Configuration
- Create a new Proxy Provider for
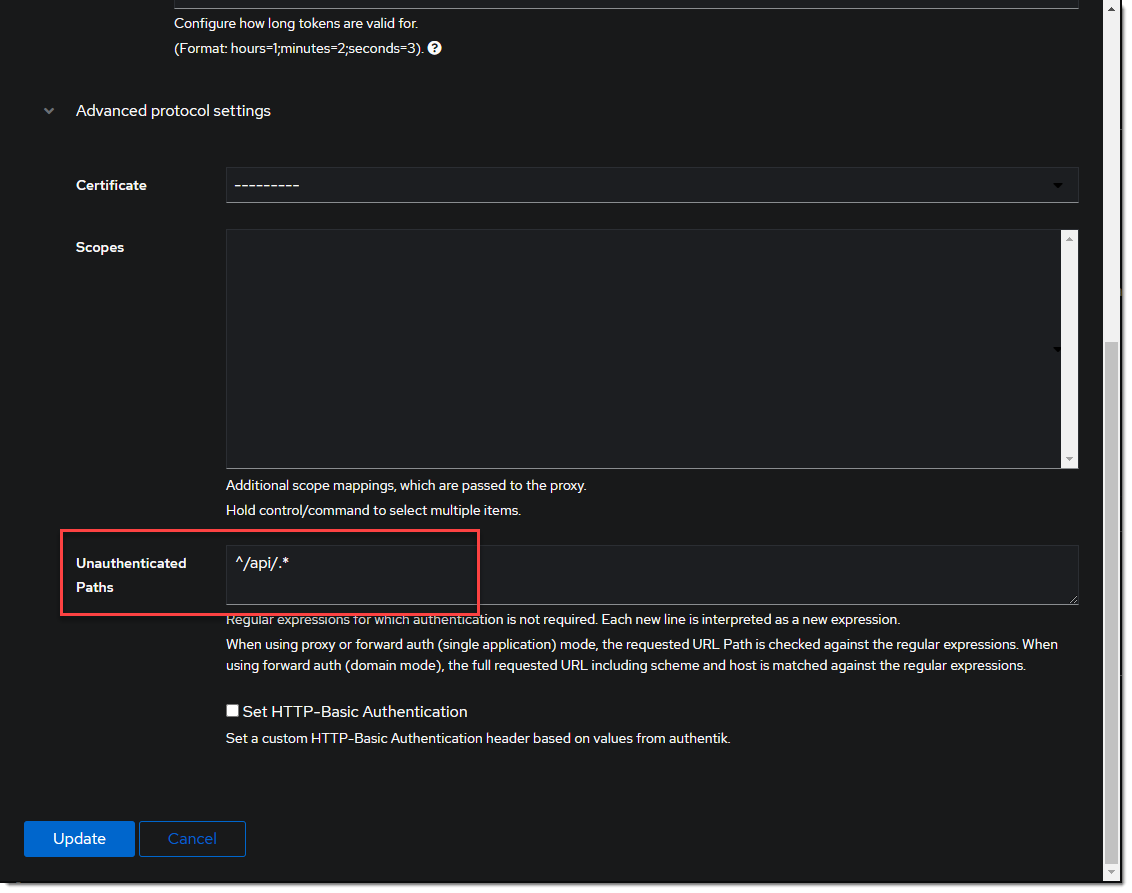
https://organizr.company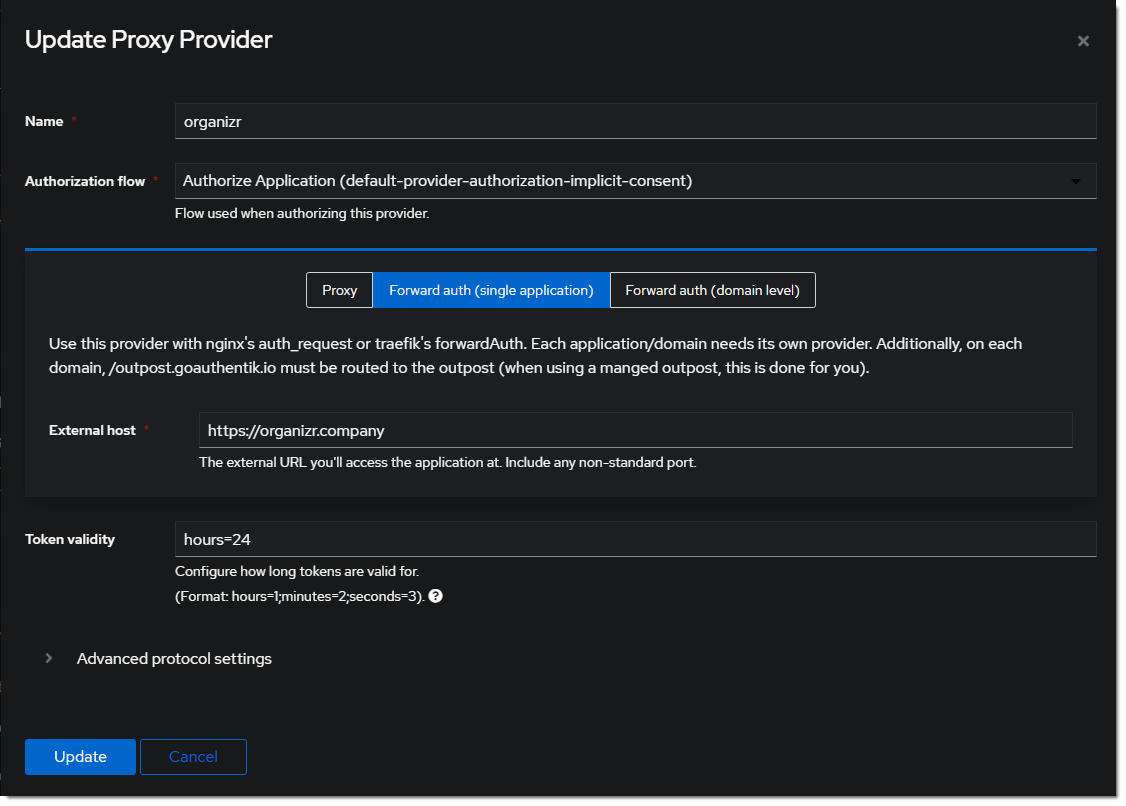 Optionally, add the regular expression to allow api calls in the advanced protocol settings.
Optionally, add the regular expression to allow api calls in the advanced protocol settings.
- Create a new Application for the
https://organizr.companyProvider.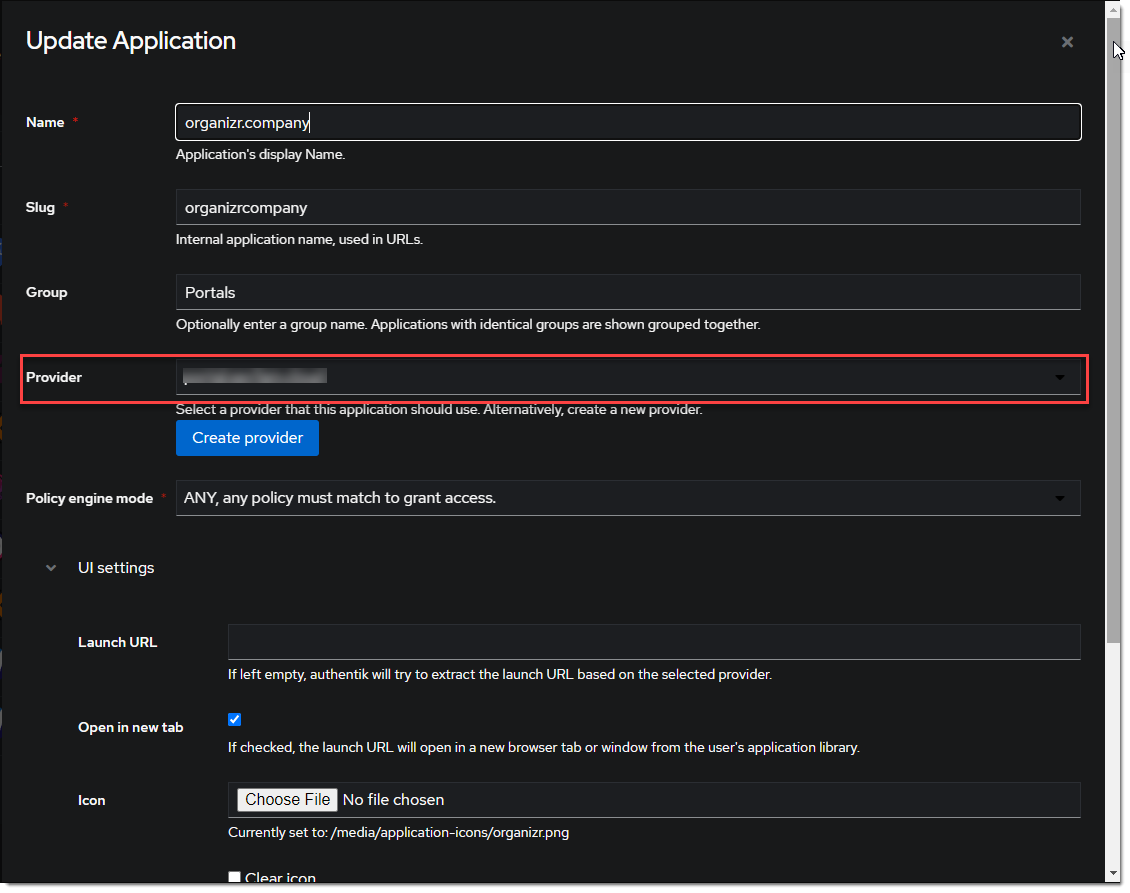 :::tip
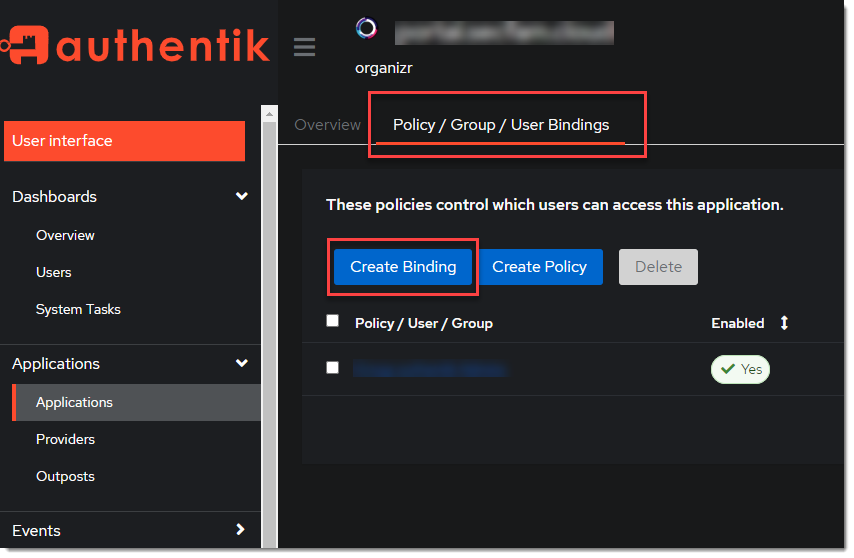
Optionally, bind the group to control access to the organizr to the application.
:::tip
Optionally, bind the group to control access to the organizr to the application.
 ::: 3. Add the Application to the authentik Embedded Outpost.
::: 3. Add the Application to the authentik Embedded Outpost.
organizr Configuration
:::caution Ensure any local usernames/email addresses in organizr do not conflict with usernames/email addresses in authentik. :::
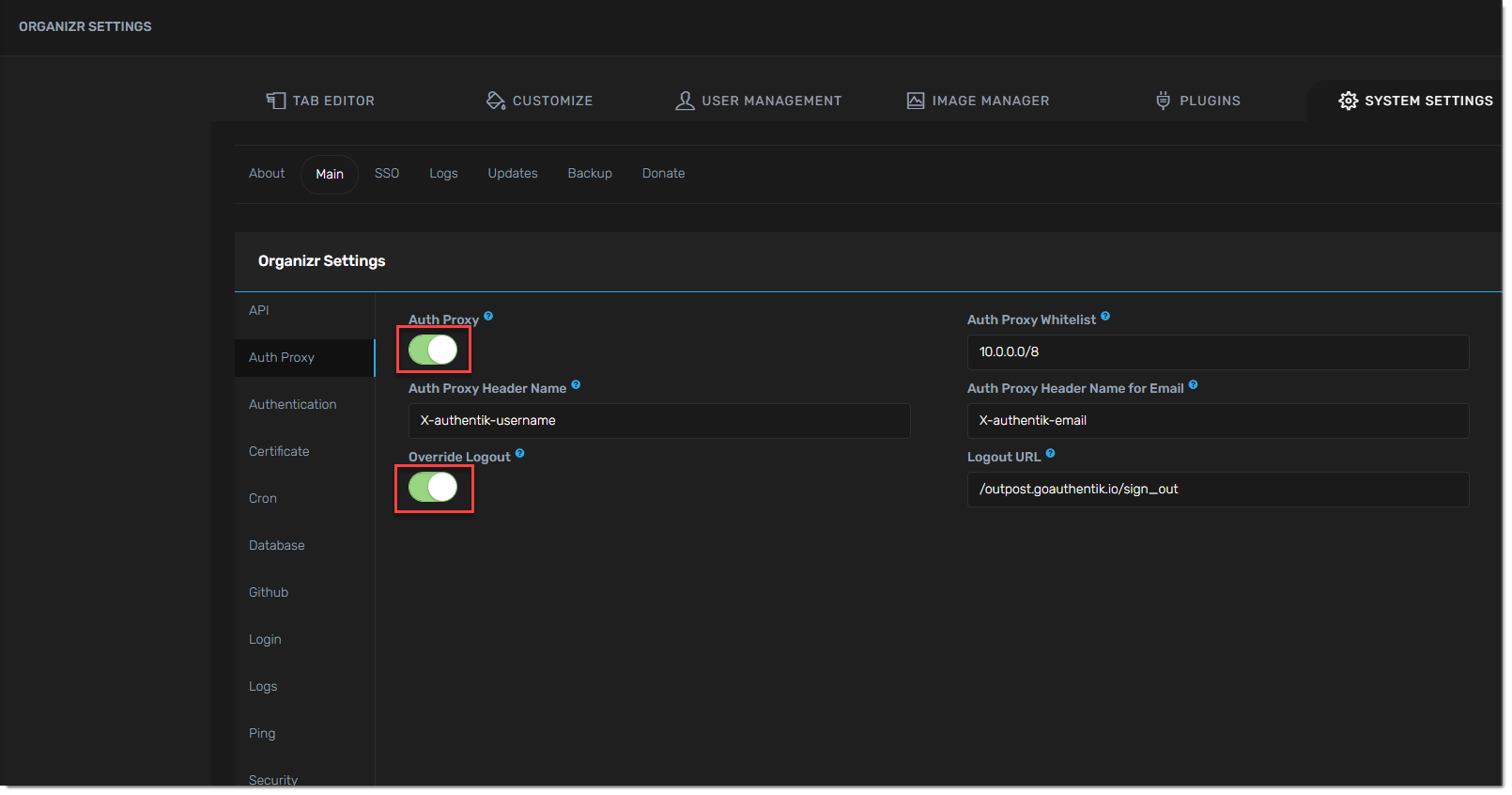
- Enable Auth Proxy in organizr system settings -> main -> Auth Proxy
Auth Proxy Header Name: X-authentik-username
Auth Proxy Whitelist: your network subnet in CIDR notation IE 10.0.0.0/8
Auth Proxy Header Name for Email: X-authentik-email
Logout URL: /outpost.goauthentik.io/sign_out
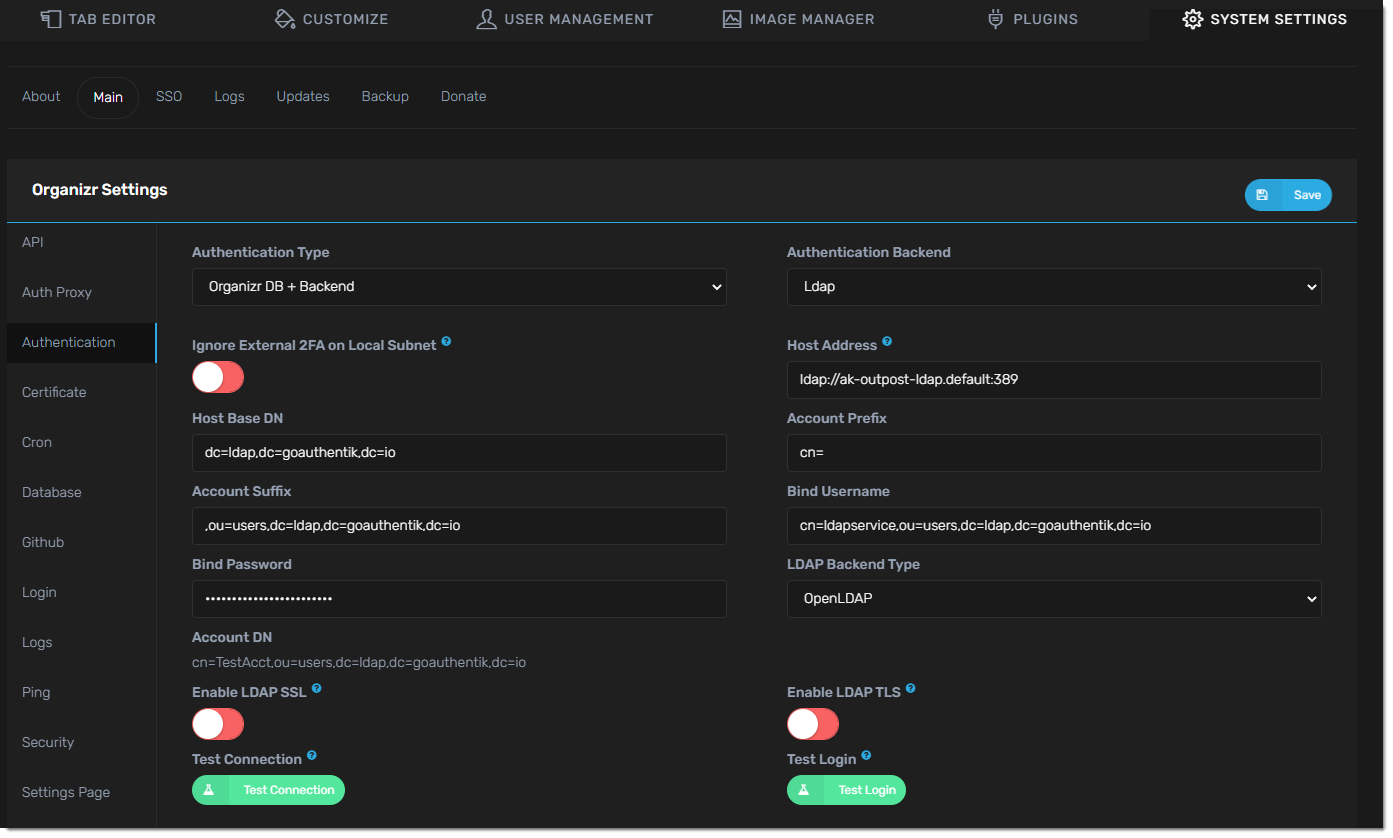
- Setup Authentication in organizr system settings -> main -> Authentication
Authentication Type: Organizr DB + Backend
Authentication Backend: Ldap
Host Address: <LDAP Outpost IP address:port>
Host Base DN: dc=ldap,dc=goauthentik,dc=io
Account Prefix: cn=
Account Suffix: ,ou=users,dc=ldap,dc=goauthentik,dc=io
Bind Username: cn=ldapservice,ou=users,dc=ldap,dc=goauthentik,dc=io
Bind Password: <LDAP bind account password>
LDAP Backend Type: OpenLDAP
:::info
Access for authentik users is managed locally within organizr under User Management. By default, new users are assigned the User group.
:::
:::tip
Consider front-ending your application with a forward auth provider for an SSO experience.
:::