3 KiB
| title |
|---|
| FreeIPA |
Preparation
The following placeholders will be used:
svc_authentikis the name of the bind account.freeipa.companyis the Name of the domain.ipa1.freeipa.companyis the Name of the FreeIPA server.
FreeIPA Setup
-
Log into FreeIPA.
-
Create a user in FreeIPA, matching your naming scheme. Provide a strong password, example generation methods:
pwgen 64 1oropenssl rand -base64 36. Once done clickAdd and Edit. -
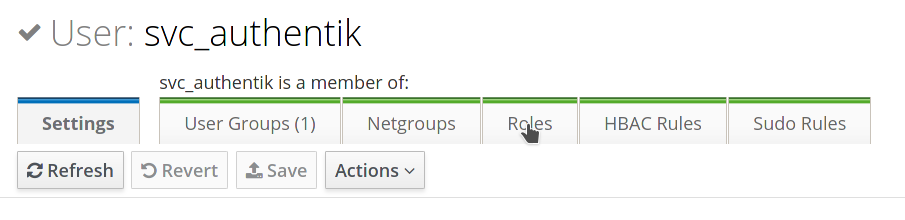
In the user management screen, select the Roles tab.
-
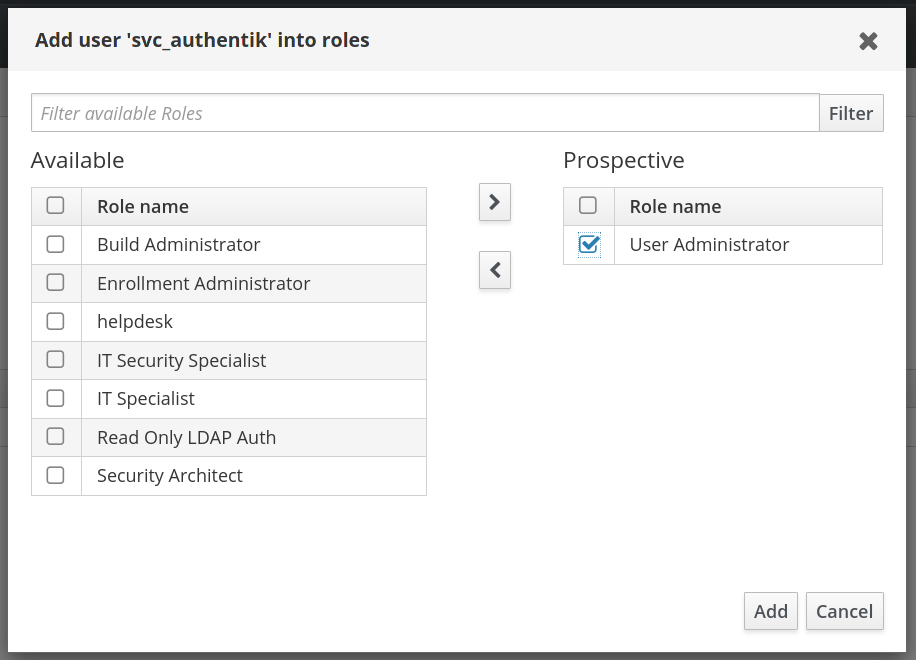
Add a role that has privileges to change user passwords, the default
User Administratorsrole is sufficient. This is needed to support password resets from within authentik. -
By default, if an administrator account resets a user's password in FreeIPA the user's password expires after the first use and must be reset again. This is a security feature to ensure password complexity and history policies are enforced. To bypass this feature for a more seamless experience, you can make the following modification on each of your FreeIPA servers:
$ ldapmodify -x -D "cn=Directory Manager" -W -h ipa1.freeipa.company -p 389 dn: cn=ipa_pwd_extop,cn=plugins,cn=config changetype: modify add: passSyncManagersDNs passSyncManagersDNs: uid=svc_authentik,cn=users,cn=accounts,dc=freeipa,dc=company
Additional info: 22.1.2. Enabling Password Reset Without Prompting for a Password Change at the Next Login
authentik Setup
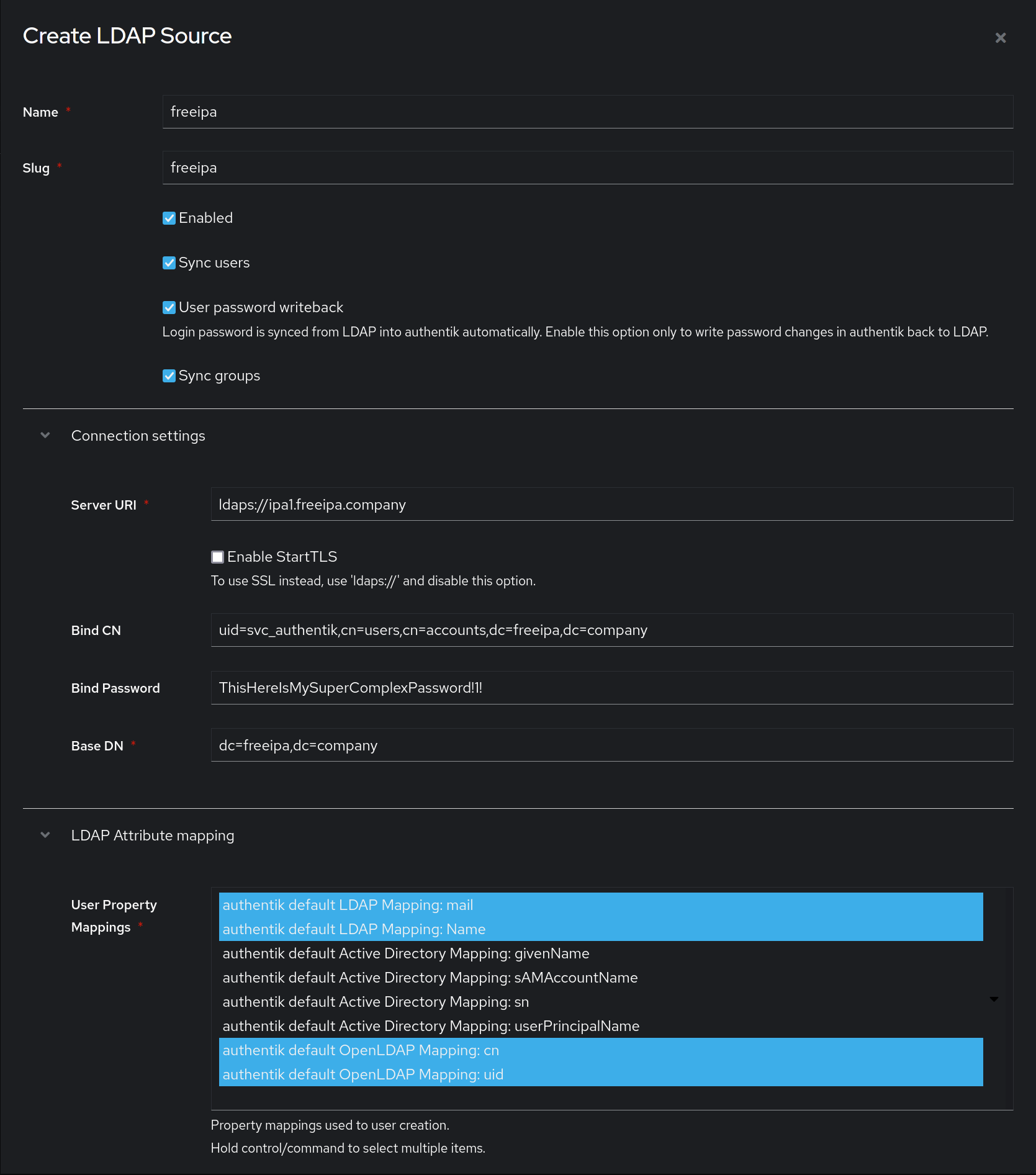
In authentik, create a new LDAP Source in Resources -> Sources.
Use these settings:
- Server URI:
ldaps://ipa1.freeipa.company - Bind CN:
uid=svc_authentik,cn=users,cn=accounts,dc=freeipa,dc=company - Bind Password: The password you've given the user above
- Base DN:
dc=freeipa,dc=company - Property mappings: Control/Command-select all Mappings which start with "authentik default LDAP" and "authentik default OpenLDAP"
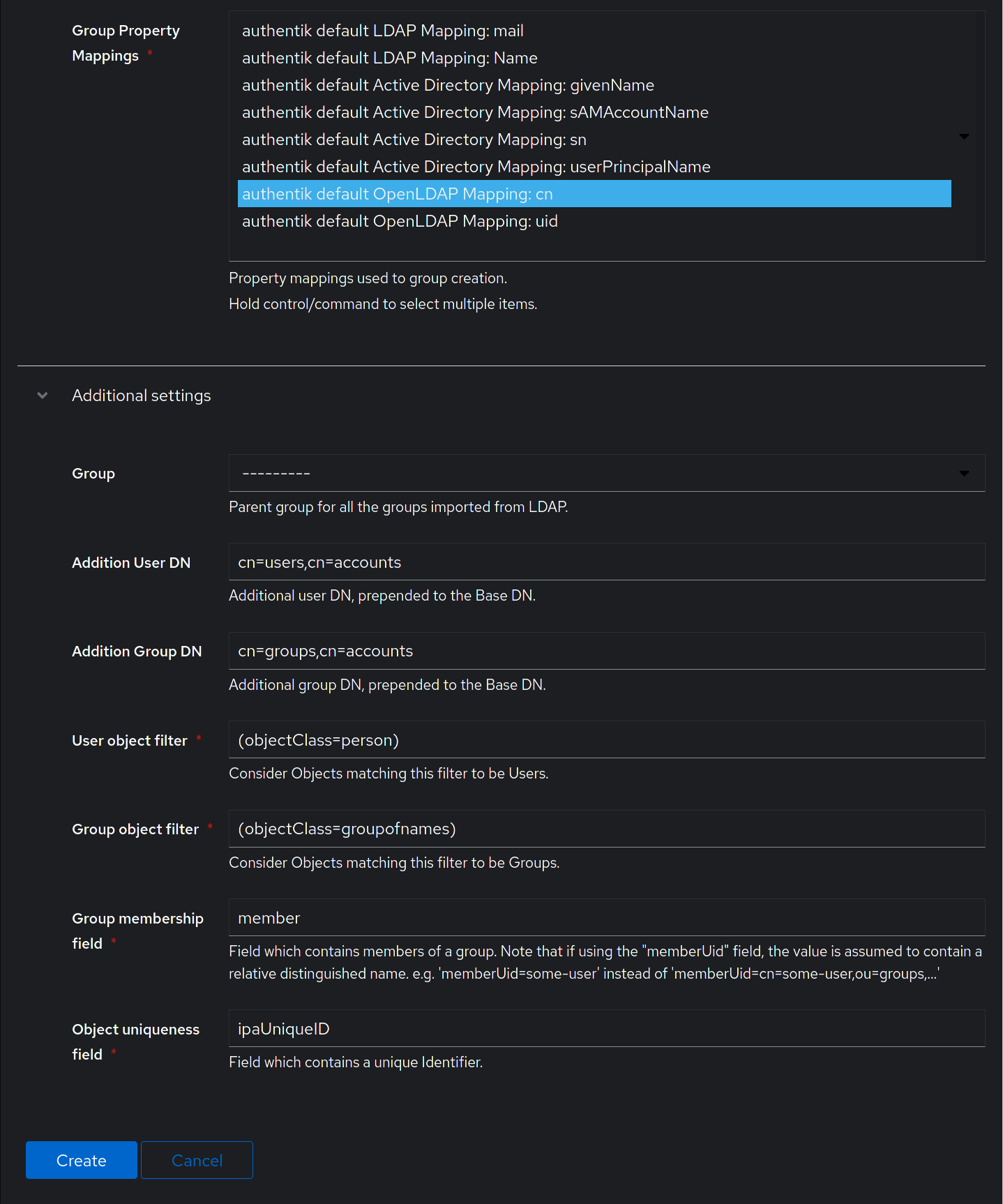
- Group property mappings: Select "authentik default OpenLDAP Mapping: cn"
Additional settings:
-
Group: If selected, all synchronized groups will be given this group as a parent.
-
Addition User/Group DN:
cn=users,cn=accounts -
Addition Group DN:
cn=groups,cn=accounts -
User object filter:
(objectClass=person) -
Group object filter:
(objectClass=groupofnames) -
Group membership field:
member -
Object uniqueness field:
ipaUniqueID
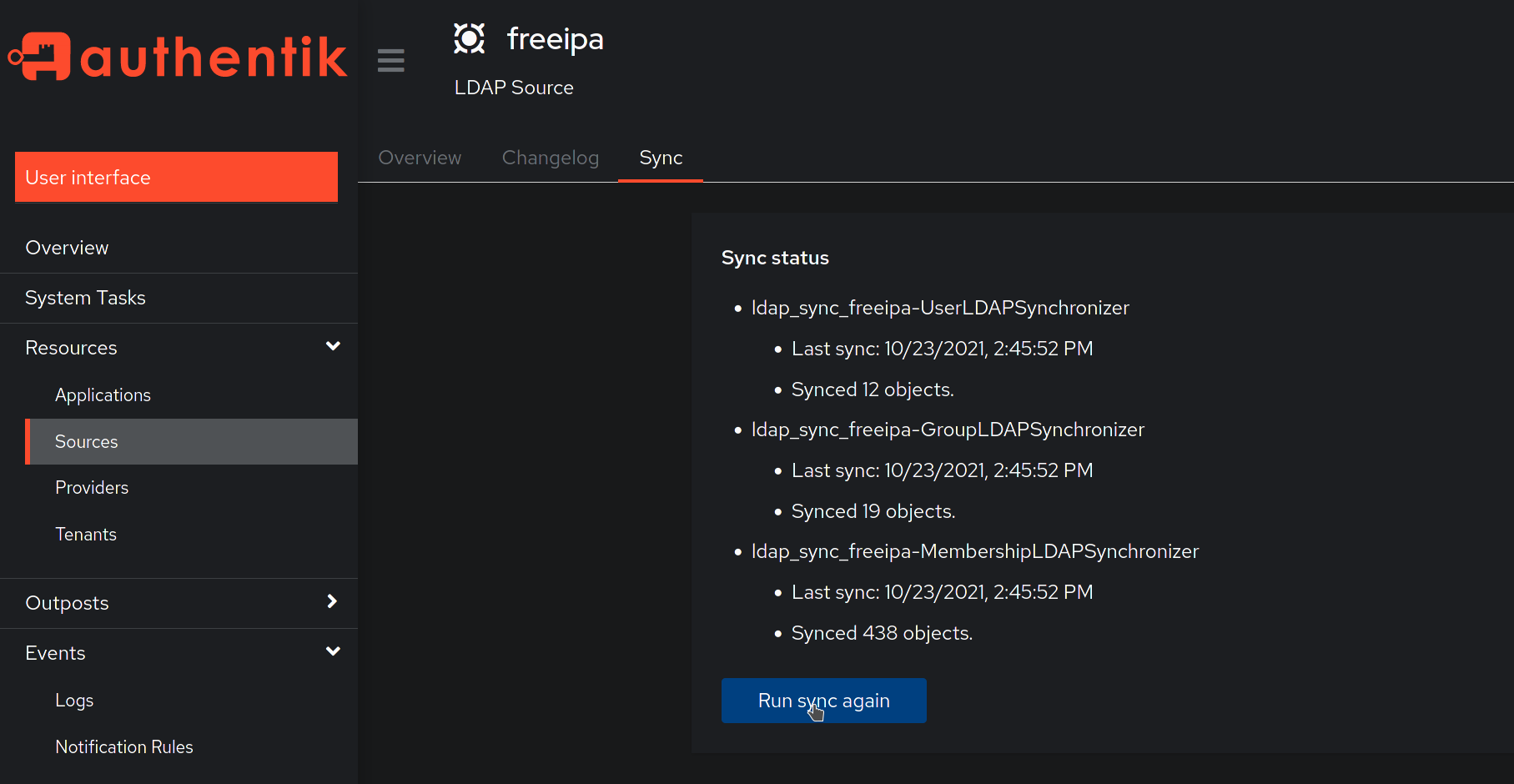
After you save the source, you can kick off a synchronization by navigating to the source, clicking on the "Sync" tab, and clicking the "Run sync again" button.
Lastly, verify that the "User database + LDAP password" backend is selected in the "Password Stage" under Flows -> Stages.